All it takes is 2 easy steps
If you're a winner, we will send you $100 Amazon gift card at Dreamforce!


If you are not a healthcare organization like a hospital or doctor’s office and you’re worried about complying with HIPAA rules, take a breath.
Although you hear “HIPAA won’t allow this” or “I can’t do that because of HIPAA rules,” the Health Insurance Portability and Accountability Act (HIPAA) does not apply in many of the cases where it is cited. For example, HIPAA only applies to “covered entities.” That means healthcare providers like hospitals, doctors, pharmacies, health insurers, and healthcare clearinghouses. It also applies to the business associates of those entities, such as companies that handle medical records as a vendor. These entities are required to keep your protected or personal health information (PHI) secure and private.
If you aren’t a “covered entity,” i.e., a healthcare provider, you aren’t affected by HIPAA rules. Instead, your disclosure of PHI may be governed by sensitivity to your customers, or other applicable state or federal privacy laws.

Sara Morrison wrote a useful guide to HIPAA – what it covers, what it doesn’t – for Vox. In it, she makes it clear that the single “P” in HIPAA does not stand for privacy. It stands for portability.
Morrison points out that the law was created in 1996 to address the massive digitization of health data that was coming, and it didn’t go into effect until 2002. HIPAA, she writes, contains “provisions to prevent healthcare fraud, simplify and standardize medical records, rules for pre-tax employee medical savings accounts, and to ensure continuous health insurance coverage for employees who lost or changed their jobs.” Privacy is addressed in the “administrative simplification” section.
Privacy concerns are the reason that healthcare providers and insurance companies might insist that you use HIPAA-compliant channels or patient portals to communicate with them.
SMS-Magic is considered a “business associate” of healthcare organizations and insurers and must take extra measures to ensure HIPAA’s protections. We also agree to sign a Business Associate Agreement and to implement controls to maintain reasonable appropriate measures for protecting ePHI. We are also considered a “Conduit from Source to Destination,” which doesn’t require a signed agreement. Our core objective is to ensure the confidentiality, integrity, and availability of all ePHI.
We do that in three areas: technical safeguards, physical safeguards, and administrative safeguards.
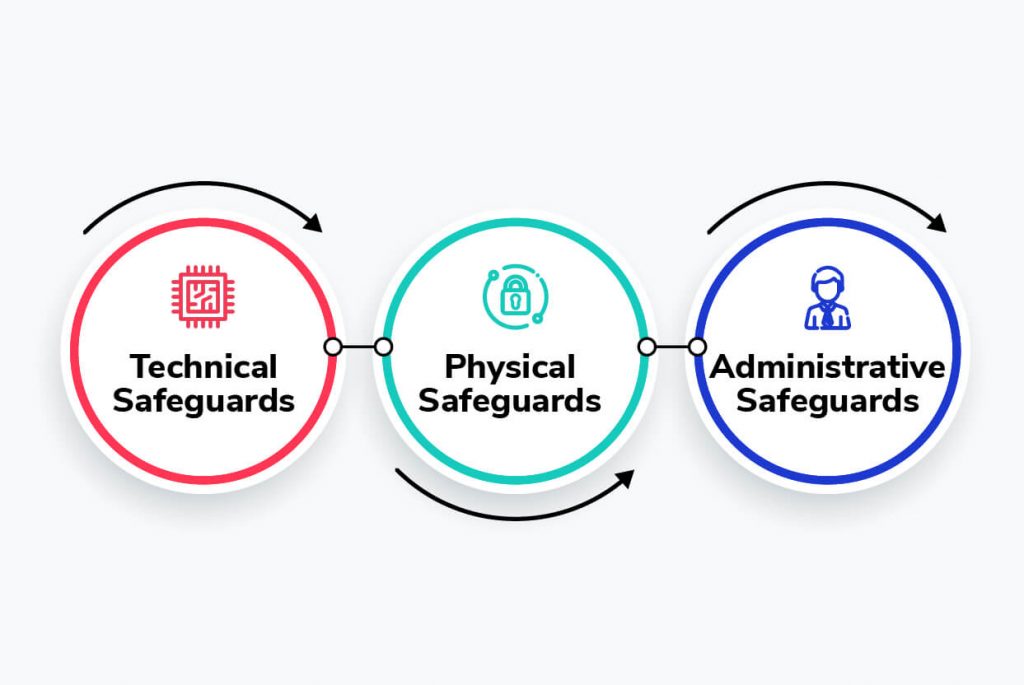
Our technical safeguards include use of access controls, integrity controls, audit controls, identity authentication, and transmission security to avoid unauthorized PHI access.
We take extra precautions to ensure the physical security of our servers and systems in the following ways:
Screen Magic administrative measures include administrative actions, as well as policies and procedures, to manage the selection, development, implementation, and maintenance of security measures to protect ePHI.
Because of the nature of our service, SMS-Magic is considered a “Conduit from Source to Destination.” That means we designed our software to transmit ePHI without retaining or accessing the information except on a random or infrequent basis. We are a conduit for your information, not a warehouse.

HIPAA regulations are in place to prevent sensitive information from falling into the wrong hands. Abiding by these rules and regulations helps protect data privacy and keeps everyone clear of fines and litigation. Although HIPAA compliance appears to be a challenge to using communication technologies in the healthcare industry, we offer a well organized, experience and compliant business as your partner.
Contact us today to help your business engage customers, capture leads, build a pipeline, and increase revenue.
Stay updated on business text messaging
Text MAGIC for Demo to
USA: 36343
AUS: (61)409564682
UK & ROW: +44 7860017509
Email: care@sms-magic.com